Practical Course Advanced Networking (Winter 2014/2015)
Details
| Workload/ECTS Credits: | 180h, 6 ECTS |
| Module: | M.Inf.805.6C: Fortgeschrittenenpraktikum Computernetzwerke (6C), M.Inf.1800.Mp: Fortgeschrittenen Praktikum Computernetzwerke |
| Lecturer: | Dr. Xu Chen |
| Teaching assistant: | Mr. Lingjun Pu |
| Time: | start:23 October 2014 14:00-16:00 |
| Place: | IfI 3.101 |
| UniVZ | [1] |
Course description
In this semester, some of our offered projects are supported by Microsoft's Hawaii project. By choosing one of the projects marked by Hawaii, you are eligible to participate in the [2]. (500 US dollars will be awarded to the most competent team within our university.)
We have some project(s) demo here for previous semesters.
Prerequisites
You are highly recommended to have attended the following course(s) prior to this one:
- Computer Networks (previously "Telematik")
Organization
Informational meeting
At the beginning of this semester (see #Schedule), there is an informational meeting.
Course teams
Students conduct this course in small teams. A team consists of at most three students.
Passing requirements
- Present your topic and demonstrate your project at the end of this course (70%)
- Prepare a written report on the selected topic (12-15 pages, Template:[3]) (30%)
- It is mandatory for all students to stick to the deadlines mentioned in #Schedule.
Presentation Schedule(26 Feb. 2015)
- Student Team Supervised by Steph Sigg 2:00pm ~~ 2:30pm
- Student Team Supervised by David Koll 2:30pm ~~ 3:00pm
Schedule
- 23 October 2014, 14:00-16:00: Informational meeting
- Introduction to the course, selection of topics, formation of teams, and discussion of open questions
- 11 December 2014, 14:00 - 16:00: Project mid-term presentation
- Give a presentation on the project topic, motivation and project plan
- Time limit: 15 min presentation + 5 min Q&A
- Presentation Schedule
- Implementation and analysis of a location-based community organizer (Hari Raghavendar rao Bandari and Seshagiri Prabhu)
- Recognition of activities and gestures from WiFi RSSI (Gipsa Joseph and Amitbhai Pethani)
- 26 February 2015, 14:00 - 16:00: Project final presentation
- Present and demonstrate your project, the motivation, the architecture, the program and the result
- Time limit: 25 min presentation (with demo) + 10 min Q&A
- 27 February 2015, 23:59: Submission of written report
Topics
The following list of topics is constantly being expanded. If there is no topic that you like at the moment, please check back regularly for the most recent updates. You can also get in touch with us directly and we will try to find a topic that interests you. Also feel free to suggest your own topic(s) to the course advisors and we will accept it if the topic satisfies the requirements of this course.
| Topic | Topic advisor | Initial readings | Description | Student |
| Large scale signal analysis | Xu ren, Mayutan Arumaithurai | Brain computer interface (BCI) lab at the Department of Neurorehabilitation Engineering focuses on decoding motor related information at the cortical level, using signals such as Electroencephalography (EEG), for the purpose of rehabilitation. In our lab, we seek to extract motor intentions (imagination or attempts) from EEG in real time, with which we use to trigger external devices (electric stimulator or robotic device) within a short latency. Currently, we are particularly interested in a special EEG signal modality called movement related cortical potential (MRCP) for the purpose of motion intention extraction. We are also working on advanced algorithms to extracting pathological signatures from EEG and EMG recordings. These signatures will also allow applying appropriate interventions. | ||
| Implementation and evaluation of 112 (emergency services) protocols | Mayutan Arumaithurai | ECRIT WG [4] | Though, the Internet and communication means have advanced, Emergency calls (i.e. 112) can only be performed by traditional phone calls. Emergency service providers cannot handle VoIP, text and video messages. Handling such messages will allow emergency service providers to scale and thereby handle large scale emergency. The task will consist of implementing and testing both client (preferably on a phone) and server side of standardized(or currently being standardized) emergency services protocols by the IETF ECRIT working group. | |
| Real time analysis of large scale data | Mayutan Arumaithurai | The team will have to apply current tools (and if possible improve them) to analyse large scale data at real time. | ||
| News recommendation system | Hong Huang | The project was asked to crawl news from internet and then recommend them to users according to their interest. | ||
| Research genealogy system | Hong Huang | The project was asked to crawl advisor-advisee relationship information from internet and get a genealogy tree for the researchers. | ||
| Implementation (and analysis) of a community organizer. | David Koll | The team will develop a location based community organizer. The idea is to share your location and activity with communities within your social contacts. If two members of a community are close to each other with regards to their location, the application will trigger events, which allow setting up meeting points, sharing contents (e.g., ratings for nearby places), etc.
Depending on the team size, after implementation, the team size should deploy the tool and collect measurements about user movements, contact frequencies, etc. |
||
| Implementation device-to-device communication via WiFi direct technology | Lingjun Pu Xu Chen | The team will first study the difference amongst bluetooth, WiFi direct and NFC and then implement client-server file transfering applications with BIO (blocking synchronous IO), NIO (non-blocking synchronous IO) or AIO (asynchronous IO) mode to analyze and benchmark the communication delay and energy cost in terms of distinct communication technology. | ||
| The Telepathic Phone: Recognition of activities and gestures from WiFi RSSI | Stephan Sigg | [5] | Activity recognition on mobile phones usually requires that the device is carried while activities are conducted (e.g. accelerometer-based). However, it was demonstrated recently that this recognition is feasible also from WiFi RSSI when activities are conducted in proximity of the phone (device-free recognition).
We will provide a mobile phone and tools to extract RSSI information on the phone and to process the data offline. The team will develop an application that can achieve this processing real-time on the phone and display the recognised activities or gestures. |
|
| Gesture and activity recognition from 2G/3G RSSI | Stephan Sigg | [6] [7] | Activity recognition on mobile phones usually requires that the device is carried while activities are conducted (e.g. accelerometer-based). However, it was demonstrated recently that this recognition is feasible also from WiFi RSSI when activities are conducted in proximity of the phone (device-free recognition).
In this project, students will develop an application to utilise 2G/3G signals for activity recognition. This work is based on the OsmocomBB project. Development phones will be provided. |
|
| Environment adaptive adjustment of audio-based security on mobile phones | Stephan Sigg | [8] | We have demonstrated a secure pairing mechanism based on fingerprints from ambient audio.
In case studies, it was observed, that the parameters of the approach need to be adapted in order to provide a good tradeoff between security and usability in environments with varying characteristics such as background noise figure. In this project, the students will derive a mechanism to automatically adapt the parameters of the audio-based ad-hoc secure pairing mechanism. |
|
| Utilising the channel as a calculator for mathematical functions | Stephan Sigg | [9] | In traditional wireless communication systems, communication load is limited for its large impact on energy resources of nodes.
However, for passive, such as, RFID, backscatter or parasitic nodes, which constitute a significant share of devices in the upcoming Internet of Things (IoT), the main constraint will be computational load rather than energy. In this project, students will develop and deploy a network of distributed nodes that compute functions on the wireless channel. USRP Software Defined Radio nodes will be provided to serve as network nodes in this project. |
|
| Bringing offline social networks on-line | Stephan Sigg | [10] [11] | Interaction with online social networks has become common in our modern society.
However, continuously updating and maintaining a profile in online social networks can become tedious. The upcoming Internet of Things may constitute the infrastructure for the next evolution of online-social networks: seamless coalescence with offline social networks. In this project, the concept of Social Centric Networking to support this development is studied and a demonstrator is developed. |
|
| Opportunistic social sensing as an enabling technology for smart cities | Stephan Sigg | [12] [13] | In recent years, with tremendous advances in areas like mobile devices, algorithms for distributed systems, communication technology or protocols, all basic technological pieces to realise a Smart City are at hand. Missing, however, is a mechanism that bridges these pieces to ease the creation of Smart Cities at a larger scale. In our previous work, an opportunistic sensing platform has been proposed as an enabling technology for smart cities.
In this project, students will develop such opportunistic social sensing platform. |
Example of a successful Student Project (Demo)
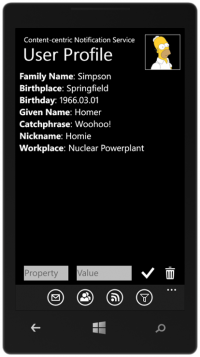
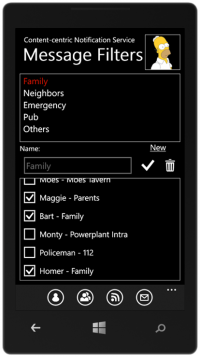
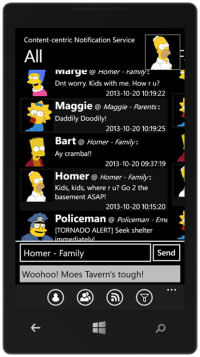
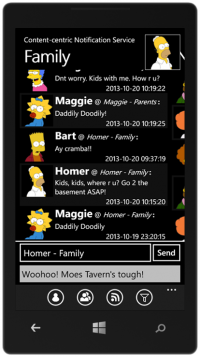
Content-centric Notification System (CNS)
A scalable, secure and timely notification system is always a necessary in daily communication. It is especially important in a disaster scenario. E.g., the government will notify the citizens about the status of the recovery, rescue and supply. The victims also need to notify their relatives (and whoever cares about them) their current status. They can also call for help (from ambulance service or any responsible service provided by the government) via such notification systems.
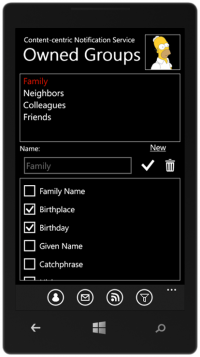
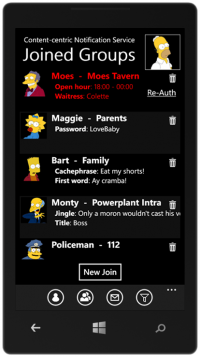
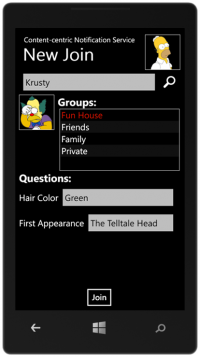
But the authorization is a big concern in such extreme scenarios. Authorization on a person-by-person basis is obviously not (energy, computation, and networkload) efficient. In such a system, we propose a new authorization system. A person create groups and use his own features (e.g., family name, cellphone number, eye color, etc.) as the challenge question for the group. In another word, he assumes that everyone who wants to join the group should have the knowledge of that information. Via such mechanism, a requester of a group can get authorization from other members of the group or even the network cache, thus save the cost on the group owner.
Another key feature of the project is the use of the Content-Centric Network (CCN). The new network architecture provides better support for a (topic-based) pub/sub system than the existing IP-based solutions. The demo system leverages the 6 machines in the network-lab running as CCN routers and hooks up with the HTTP translator on the edge of the network.
For more details, please check:
- Application definition of CNS: Media:CNSSlides.pdf.
- Architectural description of CNS: Media:CNSPoster.pdf.
- Demo abstract of CNS in ICNP 2013: Media:CNSPaper.pdf.